Security of SimpleumSafe
How SimpleumSafe protects your data
SimpleumSafe is designed so that your documents remain protected even while you work with them in everyday life – when opening, editing, backing up, and syncing. At a glance, these are the most important protective layers:
- Encrypted files and folders
- No unauthorized access from outside
- Encrypted filenames and attributes
- Encrypted cloud
- Encrypted synchronization
- Encrypted backup
- Encrypted photography
- Encrypted scanning
- Encrypted document view
- Encrypted full-text search
- Encrypted editing of documents
- Encrypted image viewer
- Assistance with password quality
- Passwords are not saved
- Biometric authentication
- Screen protection
- 2-factor authentication (Mac)
- Checking the app for manipulation every time it is started
The security concept of SimpleumSafe with continuous encryption and minimal opening to the outside is unique.
Open Safe with password, Face ID or Touch ID
Your Safe password is the main key to your data. With SimpleumSafe you can create multiple Safes; each has its own password. You can only open a Safe and decrypt files with your Safe password.
SimpleumSafe does not save these passwords and cannot reconstruct them. Even Simpleum Media GmbH and its employees cannot reconstruct the Safe password.We therefore recommend that you set up a recovery password immediately after installing SimpleumSafe. You can find instructions here.
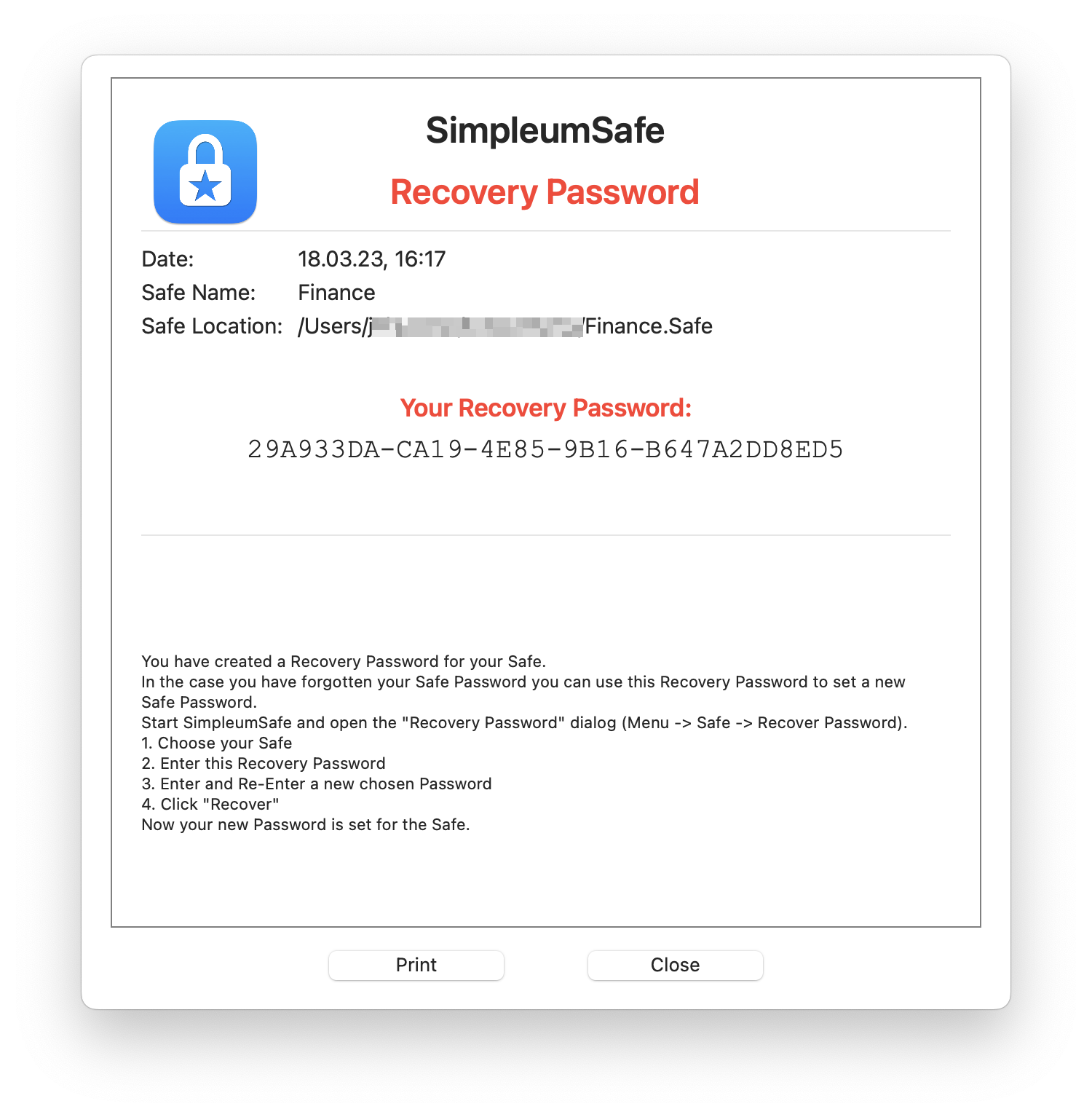
Recovery Password / Digital Legacy
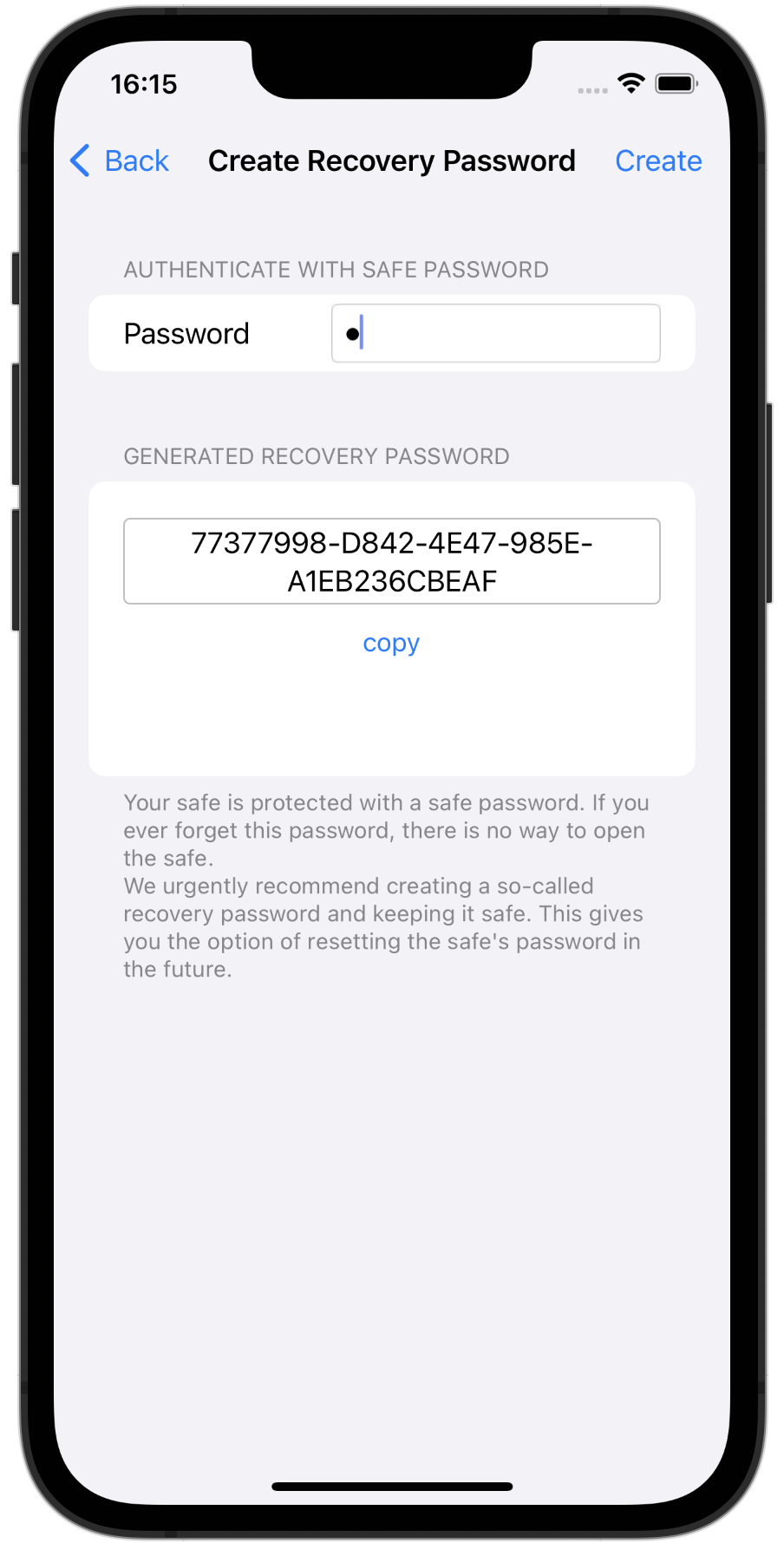
Just like a real Safe has a spare key, you can also create a recovery password that can be used like a spare key.
You can print out this second password and keep it in a Safe place. If you ever forget your password, you can create a new Safe Password using your recovery password.You can also use the recovery password to access your digital legacy or in case of an emergency. You can give the printout of the recovery password to a person you trust or to a notary, or enclose it with your will.
We recommend that you generate the recovery password immediately after you have created your Safe. You can find instructions here.
Important: Without a recovery password, SimpleumSafe cannot restore your Safe password – keep it as carefully as a physical spare key.
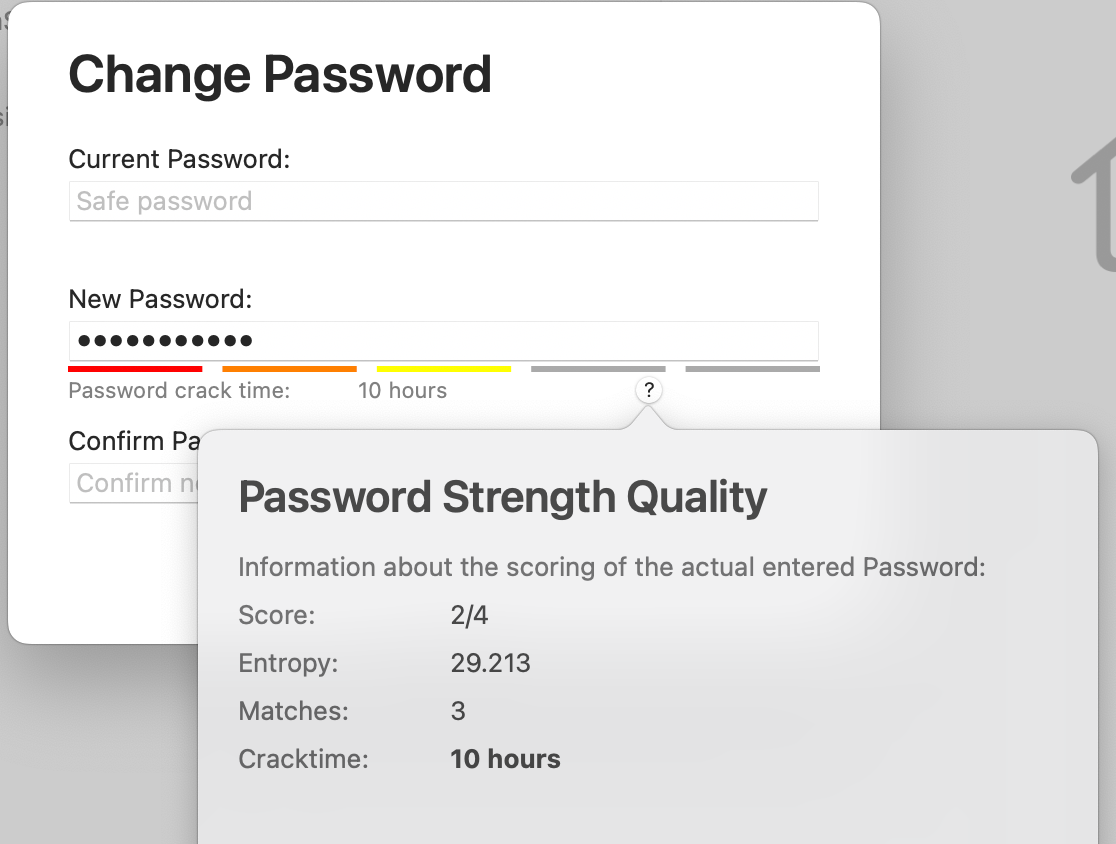
Help for a secure password
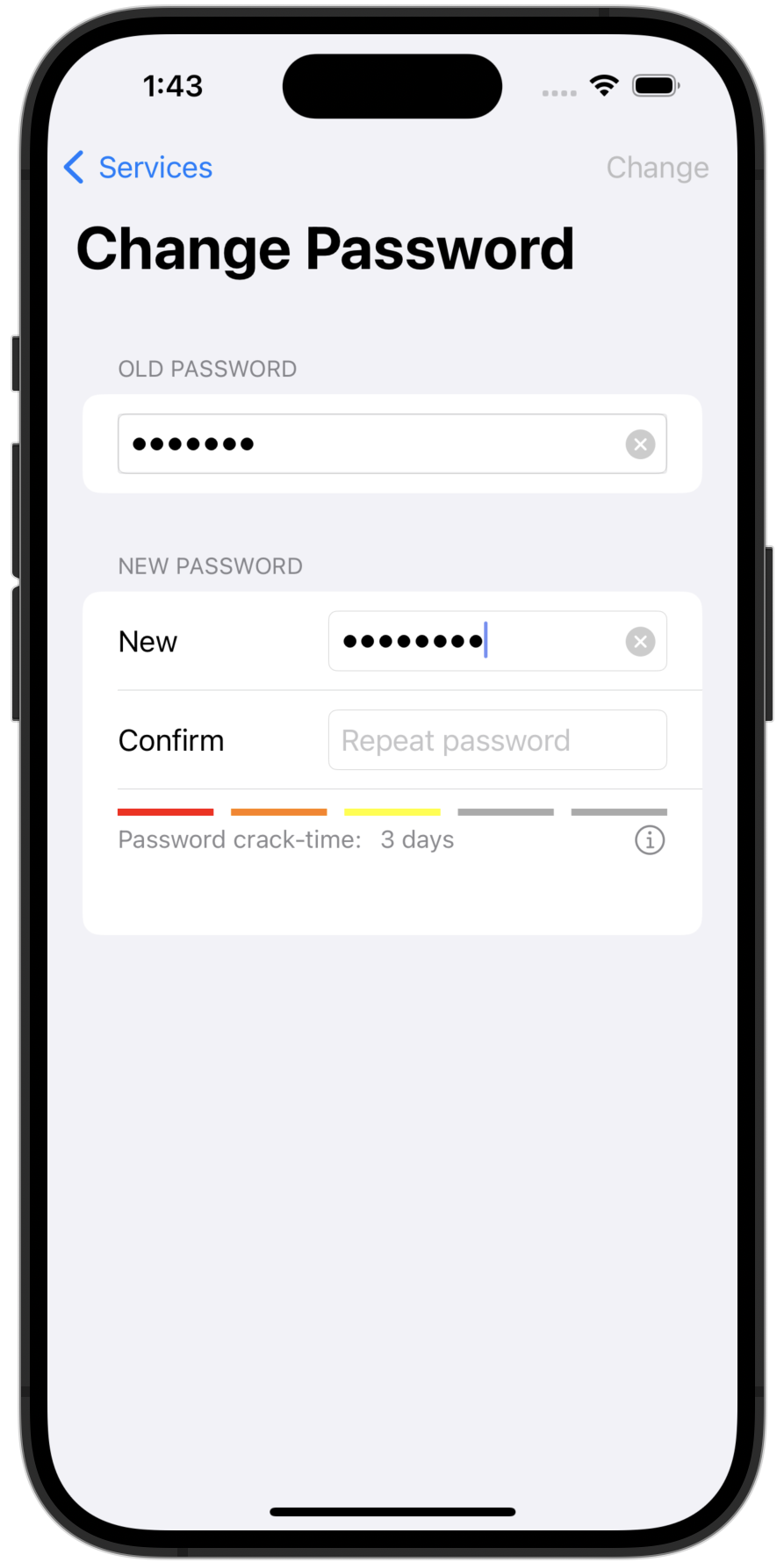
Even the best encryption algorithm won’t help if the password you use is easy to guess. SimpleumSafe evaluates the quality of the password you enter and estimates how long it would take to “crack” it – giving you immediate feedback about your password strength.
If an incorrect password is entered into SimpleumSafe, there is a time delay until you can next enter a password (2 seconds for the first failed attempt, then 4 seconds, 8 seconds, 16 seconds, etc.).A secure password protects you from being guessed through careful trial and error. SimpleumSafe supports you in choosing a strong password by making weak choices visible and slowing down repeated attempts.
If you would like to find out more about the topic of “secure passwords”, read our blog post.
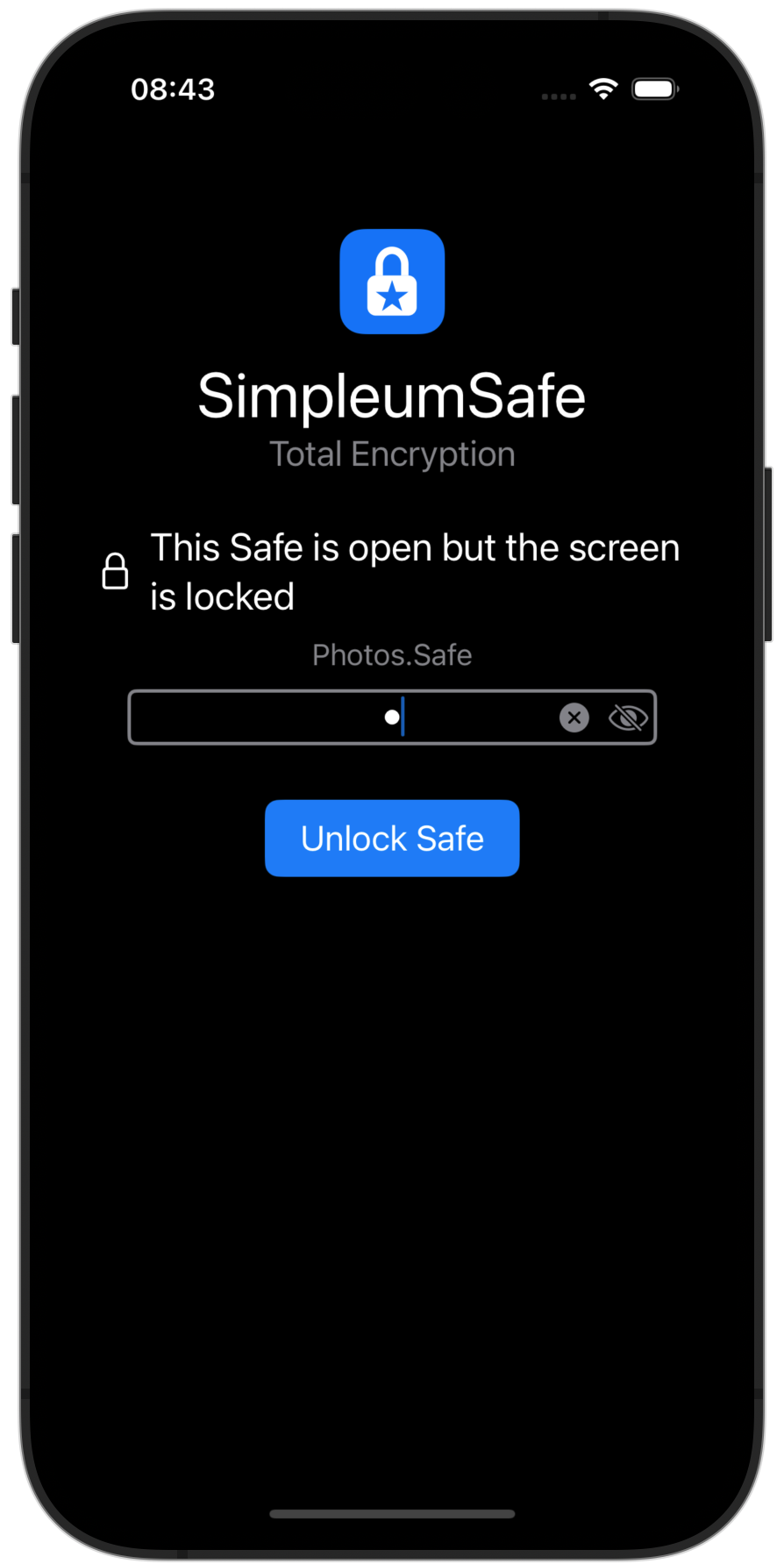
Lock Safe (e.g. in case of inactivity)
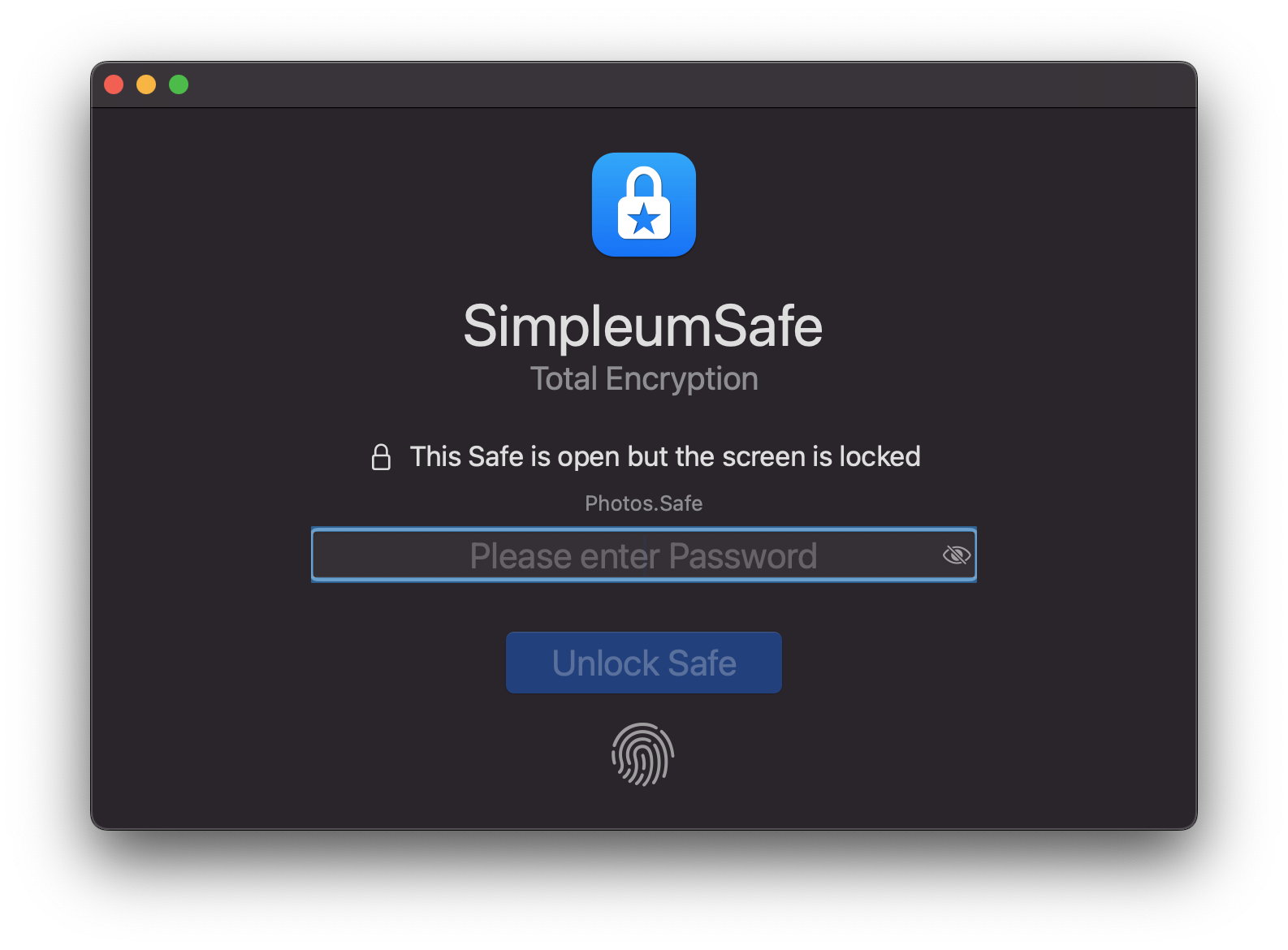
Locking the Safe when you step away keeps your data protected, without interrupting ongoing work.
By keeping the Safe open but the screen locked, SimpleumSafe ensures your data remains protected while remaining accessible for ongoing tasks. It’s a mix of accessibility and security.
Your data operations do not have to be interrupted. Whether you’re importing large amounts of data or syncing files, these tasks continue seamlessly even when your screen is locked.
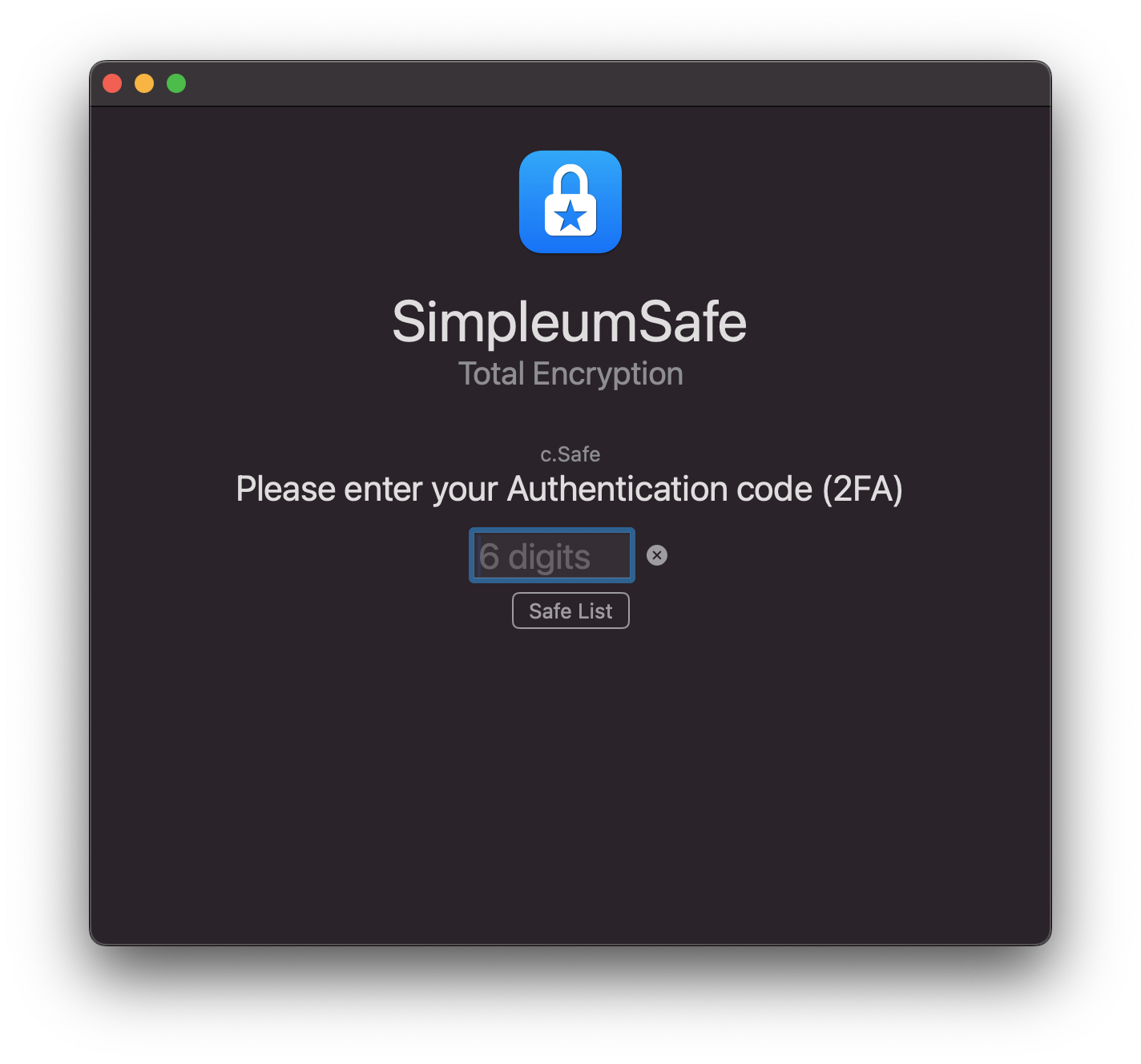
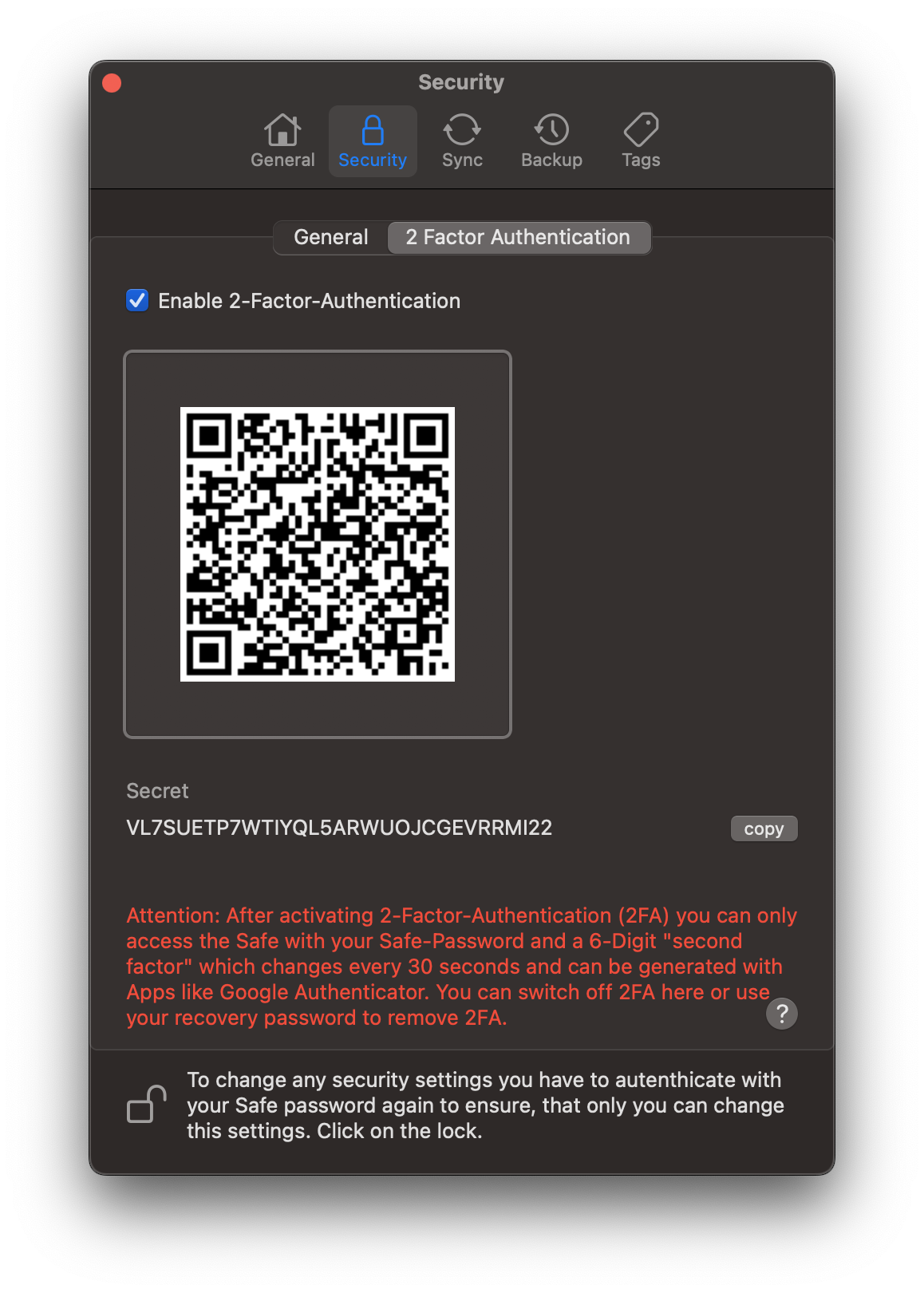
Optional 2-Factor Authentication (2FA) - Mac
With optional 2FA you add another Security layer to your Safe: even if someone knows your password, they still need a second factor to gain access.
-
Double Layer Security: After the password or biometric verification, 2FA acts as a second line of defense and requires a unique six-digit code. This adds an extra check to ensure your Safe remains protected.
-
Advanced Security: The biggest advantage of the 2FA feature is its ability to provide an additional layer of security, making unauthorized access extremely difficult. It’s not just about what you know (your password), but also what you have (your second factor).
-
Dynamic Protection: The One Time Password (OTP) is not static; it changes every 30 seconds. This dynamic makes targeted attacks significantly harder.
-
User-Friendly: The six-digit OTP is simple and effective, offering the perfect balance between ease of use and security. And since the OTP changes every 30 seconds, the risks of static passwords are eliminated.
-
Compliance and Best Practices: Implementing 2FA aligns with global cybersecurity best practices and can help meet compliance requirements, which is critical for professionals and businesses.
-
Affordable Security: Since no additional hardware is required, this feature is an affordable security upgrade. Your smartphone is your second factor, there are no additional costs.
-
Ensuring your security for the future: As cyber threats evolve, so should your security measures. The 2FA feature is a step towards securing your digital safe against emerging threats.
Nobody else sees your data
Your data belongs to you – nobody else can see it.
Would you like to keep your personal or business data safe? SimpleumSafe uses strong encryption with AES-256 and is designed for security and confidentiality throughout. Only you can decrypt the data because only you know the password used to encrypt the files in the Safe.
Even with today's fastest supercomputers it is practically impossible to decrypt your Safe just by trying out keys.
Always encrypted – at every step
In SimpleumSafe, your files are encrypted at every step:
- when they are stored in the Safe
- when you open, edit, or move them
- when you view them, even in full-screen or slideshow
Decryption only happens where it is needed – in memory – and never as plain text on disk. This keeps your data protected even if a device is lost or compromised.
Strong encryption
Your data is protected with the same encryption technology trusted by banks, governments, and industrial companies.
- Industry standard AES-256
- Widely deployed and considered secure for many years
- Approved for use at the highest U.S. “Top Secret” classification
High Security Sync
Sync like a high-security container – your encrypted data travels, the keys stay with you.
- End-to-end encrypted synchronization between your devices
- The key file is never transmitted through the cloud
- Even if someone copies your cloud data, it is useless without the missing key
- Extra protection even if a password is compromised or cloud services are attacked
Technical information
Are you an IT professional or security reviewer and want to dive deeper into how SimpleumSafe works?
The SimpleumSafe Technical White Paper describes cryptography, architecture, key management, storage formats, and the overall security model in detail.